- Recruitment software
- Solutions
company size
Featured Industries
- Resources
- Contact
- English
Use Role-based Access Control (RBAC) as a systematic solution to give users access to digital resources based on their roles. This saves you from having to manage each user separately. Instead, you classify users based on their responsibilities and roles. This makes it clearer and simpler to manage.

Role-based Access Control, most of all, is simple. You can assign users to roles in 3 clear steps to easily manage who has access to what. So you can maintain a (very) high security standard in no time.
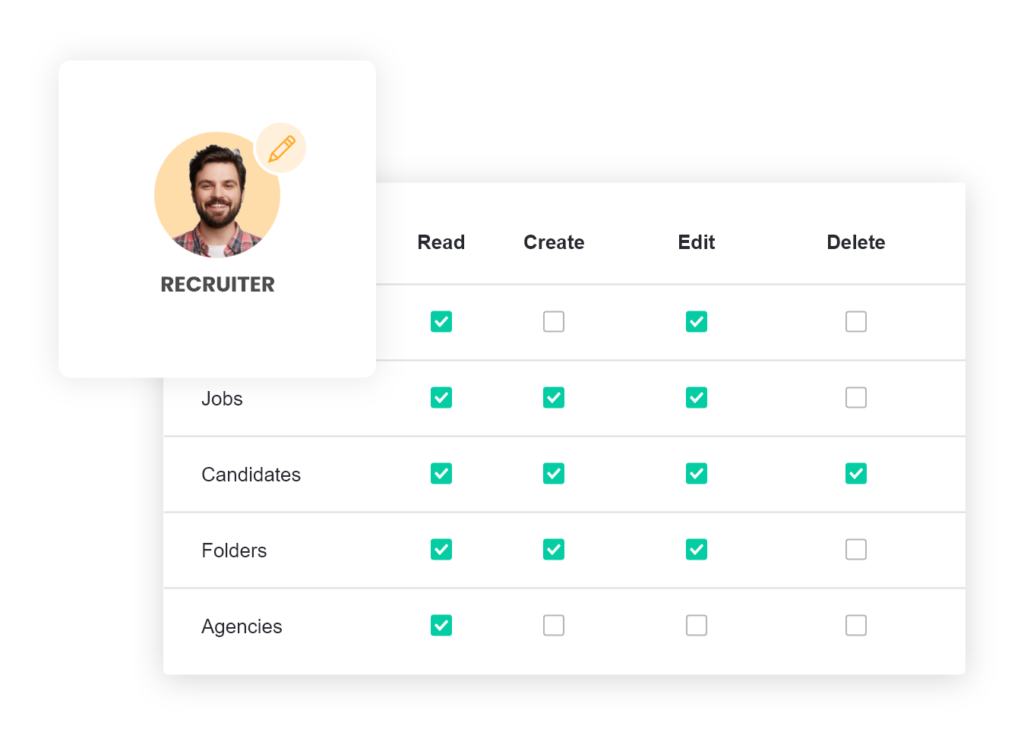
Define the different roles, such as a ‘recruiter’, ‘hiring manager’, ‘interviewer’ or ‘functional manager’. These roles form the basis for the permissions you grant users within RBAC.
Assign access permissions to the roles. Determining per screen, per section or per option whether the role has access, and if they can enter, modify and/or delete data. Ubeeo has a number of standard roles available that you can use immediately or adjust according to preference.
Assigning users to their roles. This way you determine what (access) permissions they have. Ubeeo can automatically assign most users to the correct role, thanks to integration with HR systems such as ADP, AFAS and Visma | RAET. Or use identity and access management systems, such as Identity Access Management (IAM).
Thanks to centralised management in RBAC, you have far more control over access and permissions for users. And if you want to update a role, for an integrated solution with a new tool for job vacancy campaigns, for example? This can be done in one go, after which all recruiters can create campaigns.

Combine our fresh web design with seamless integration.

Thanks to Role-based Access Control for our recruitment software, it requires far less manual changes. This prevents errors and unintentional changes in permissions.
Use RBAC for the principle of ‘least privilege’. You then only give users access to the minimum required settings. This guarantees better security, because users do not have access to data or systems that they do not need to use.